Cyberattacks on unpatched on-premises Microsoft Exchange Server have increased recently. Exchange Servers that are still not upgraded or updated with the latest cumulative and security updates are being hit by various ransomware, such as LockFile, Black KingDom, REvil, etc.
In March 2021, a state-sponsored group called Hafnium attacked Exchange Servers and compromised more than 30,000 organizations worldwide. They exploited the ProxyLogon vulnerability to compromise vulnerable Exchange Servers, install web shells, backdoors, and ransomware.
Later, other ‘proxy’ RCE vulnerabilities, such as ProxyShell, ProxyOracle, and ProxyToken, were disclosed by various researchers. Although Microsoft has released updates to patch these vulnerabilities, there are still thousands of unpatched Exchange servers vulnerable to exploitation and malicious attacks.
If your Exchange Server has been hit by ransomware, it might not be too late, and you may still recover your data, such as mailboxes, from your compromised Exchange Server to a new server.
In this blog, we have discussed what you need to do if a ransomware attack hits your organization.
What to Do If Exchange Server Hit by Ransomware?
Ransomware is malicious software installed by the threat actors on a compromised Exchange Server to prevent you from accessing the data. It encrypts the data on the server and adds a custom extension to the files, and holds it until the ransom is paid. The encrypted files cannot be decrypted without the key known only to the threat actors.
However, there are a few stages of ransomware attacks before it starts encrypting your data.
- Initiation of Ransomware Attack
- Ransomware Instantiation
- Ransomware Activation
If you detect the ransomware early, i.e., before its activation stage, you can prevent it from encrypting your data and spreading it into your network or other devices.
Follow these steps to remove the ransomware from your system and recover the data before it gets too late.
Reboot System to Safe Mode
Safe Mode is a special Windows startup mode that loads the basic Windows with limited files and drivers required for the operating system to work. It is used to troubleshoot common issues and bugs in Windows operating system. Programs configured to start automatically on boot do not start in Safe Mode unless an autorun entry is created in the Windows registry keys.
However, you can boot the Windows Server into Safe Mode with Command Prompt, stop the malicious processes, and remove the registry entries created by ransomware to prevent further damage.
To reboot the system in Safe Mode,
- Click Start> Power, then hold the Shift key and choose Restart.
- Choose to Troubleshoot>Advanced options> Start-up Settings and then click ‘Restart.’
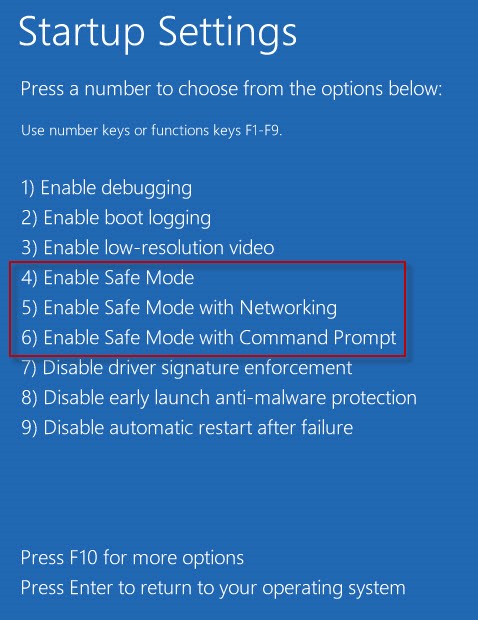
Choose Enable Safe Mode with Command Prompt from the option.
In the Command Prompt window, type taskmger.exe and press Enter to open the Task Manager.
- Click the ‘Processes’ tab and close or end the malicious processes.
- Close the Task Manager and run ‘Regedit in Command Prompt window to open Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows NT/CurrentVersion/Winlogon/Shell.
- Right-click on Shell and change the value to explorer.exe and then click ‘OK’.
- Close the Registry Editor window and run shutdown –s –t 0 to shut down the system and restart it normally.
NOTE: Some ransomware, such as REvil, can work and encrypt files even in Safe Mode.
Run Antivirus Scan
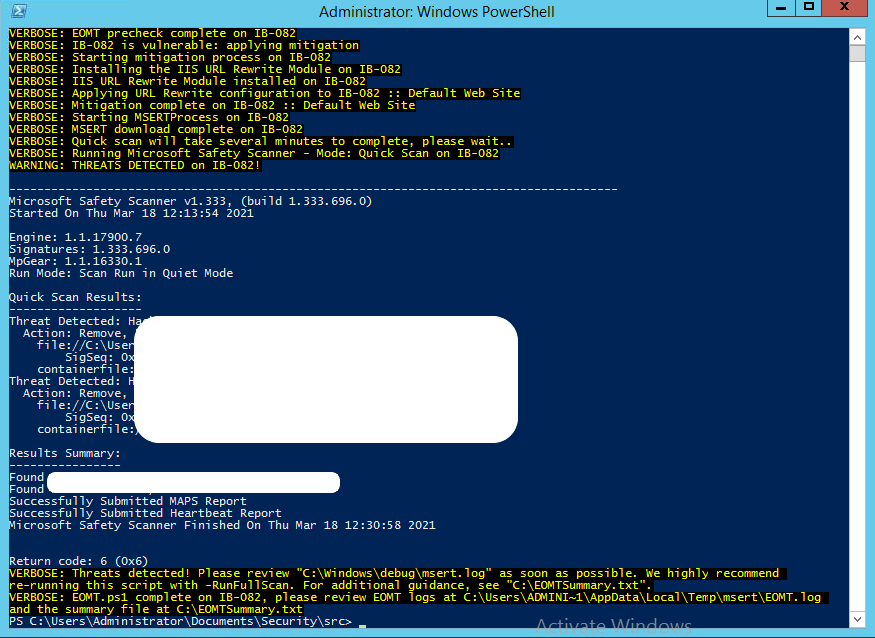
After reboot, run the anti-malware or antivirus scan using an Exchange-aware antivirus tool. You may use Windows Defender or use the One-Click Microsoft Exchange On-Premises Mitigation Tool (EOMT) to mitigate against the known attacks and remove web shells or other malicious programs installed by the attackers from the system.
The EOMT runs the Microsoft Safety Scanner program that finds and removes malware and web shells from your server machine. To run EOMT on your Exchange server, follow these steps,
- Download the EOMT.ps1 PowerShell script on the server or system connected to the Domain.
- Open Exchange Management Shell (EMS) and navigate to the EOMT.ps1 file location using the cd command.
- Then run the following command in the EMS,
.\EOMT.ps1
- This runs the Microsoft Safety Scanner (MSERT) in Quick Scan mode to find and remove threats, such as ransomware installed by the attacker.
- You may run the MSERT scan in full scan mode using the following command,
.\EOMT.ps1 -RunFullScan
Install Updates
After cleaning the server, install the latest cumulative updates and security updates released by Microsoft. For more info, refer to Microsoft Exchange Remote Code Execution Vulnerability Flaws and Their Fixes.
Conclusion
Even if you are able to clean your server from ransomware, you should avoid using your compromised Exchange Server and move the mailboxes to a new server as the threat actors may have installed backdoors. They can use these backdoors to compromise your server again even if the server is patched with the latest security updates.
You can use your backup to restore the mailboxes on the new server or install Exchange recovery software, such as Stellar Repair for Exchange, to recover mailboxes from the database of the compromised Exchange Server and save them to PSTs. You may also use the software to directly export the recovered mailboxes from a compromised server to a new Live Exchange Server or Office365. The software comes in handy when the Exchange database is corrupt, or backup is unavailable, does not work, and becomes obsolete.